Security and Cybersecurity
Why It Matters
Cybersecurity has become a crucial element for protecting information, critical infrastructures, and personal data. Cyberattacks are carried out by a variety of actors with different motivations. These attacks can cause significant damage to businesses, governments, and individuals, including direct costs such as ransom payments, data loss, and operational disruptions, as well as indirect costs like reputational damage and loss of customer trust. Additionally, the volume of attacks has increased with digitalization and the adoption of emerging technologies such as cloud computing, the Internet of Things (IoT), and artificial intelligence. The COVID-19 pandemic has further accelerated this phenomenon, increasing the attack surface due to remote work and reliance on digital services.
Attack Points
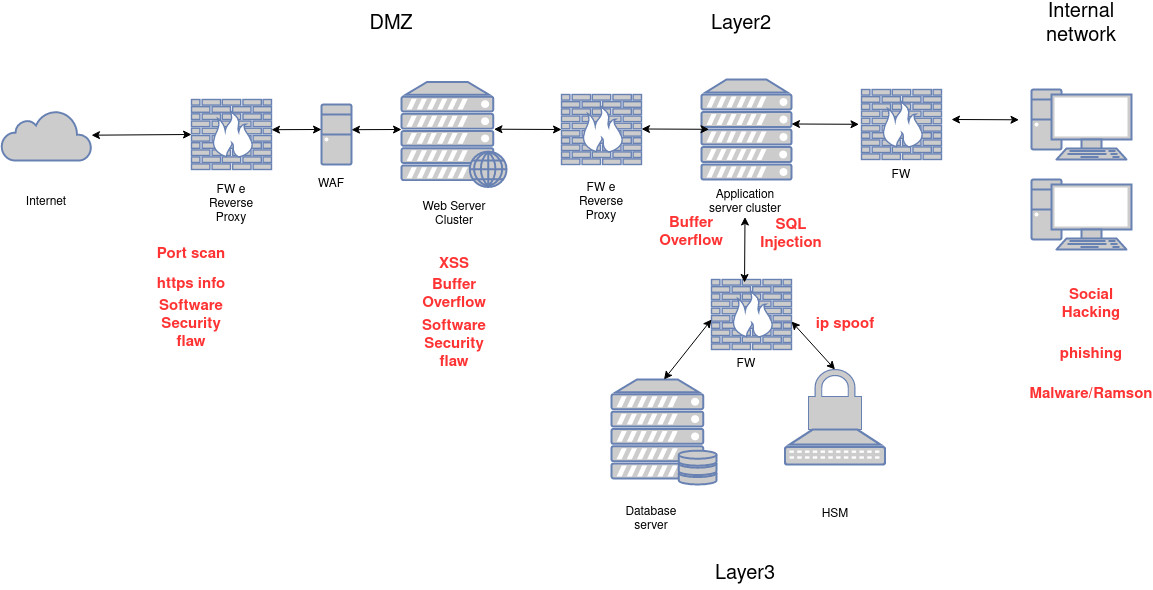
In a typical corporate organization, the infrastructure is protected by various hardware/software devices, indicated in the diagram as FW and WAF, referring to Firewall and Web Application Firewall, respectively. Their task is to regulate and analyze network traffic to prevent potential attacks. The diagram highlights common cyberattack points. Many infrastructures are well-protected against external attacks, but based on our experience, internal attacks—marked on the right as Social Hacking, Phishing, and Malware/Ransom—are often the most effective. This is because they target the still-weakest link in any security system: the human factor.
Our Security Assessment Services
We offer a variety of scanning services at all levels—whether infrastructural, software-based, or social. After an initial assessment to establish the baseline security level, we can:
- Conduct external security scans using our remote servers (black box scanning)
- Perform testing and verification across all software layers (applications, APIs, mobile apps)
- Carry out internal scans and network device assessments
- Conduct social hacking simulations
Furthermore, if the client wishes, we can perform a full Red Team assessment, attempting to bypass (and thus test) all levels of corporate security, including controlled access points, secure rooms, and video-monitored entrances. This approach provides clients with a clear evaluation of all vulnerabilities and a plan to correct them before a real attack occurs.
Performance Analysis
In addition to security scanning, we offer application and infrastructure load testing services. We can create customized load tests for the client’s platform and test it using our cloud-based control centers. During the tests, we provide real-time data to help correct anomalies and optimize overall system performance.

